I've been messing around with crawling the netdb with snex to see whats out there. Found 2 destinations this way that gave us access to add torrents through a web panel. If this can be done, be prepared to receive clown porn, maybe a podcast or show for good measure
The second case also gave us access to the router console, torrents were added through snark. A message was sent and they seemed to have fixed it now. I don't think any "real" damage was done (we did try to get access to filesystem) besides changing the router console language to spanish. Also, susimail will leave the username available this way, very dangerous obviously, as this allowed us to link the ident with an ip address obtained from the router console as well as see any services they were hosting.
http://git.simp.i2p/simp/clowning
please use auth / encrypted leasesets
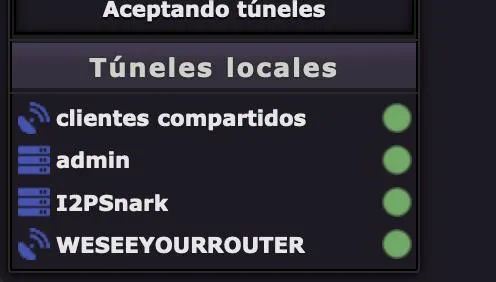
aaa wrote
Can you explain what you're doing in more detail and advise how to protect yourself from it?